1. About this document
It is split into five main sections, covering:
- general information about the practice
- the practice’s processes and activities and their roles in the service value chain
- the organizations and people involved in the practice
- the information and technology supporting the practice
- considerations for partners and suppliers for the practice.
2. General information
2.1 Purpose and description
Key message
The purpose of the IT asset management practice is to plan and manage the full lifecycle of all IT assets, to help the organization:maximize valuecontrol costsmanage riskssupport decision-making about the purchase, re-use, retirement, and disposal of IT assetsmeet regulatory and contractual requirements.
In support of the organization’s specific business objectives, the IT asset management (ITAM) practice ensures:
- good handling of the IT asset lifecycle:
- from planning to disposal in collaboration with other IT and non-IT practices
- with appropriate effort considering the financial and corporate value of the IT assets so that the:
- IT assets and related contracts deliver value at reasonable cost and acceptable risk
- IT assets are secure, reliable, and available.
- information about IT assets and related entities (such as contracts and vendors) is trustworthy, accurate, complete, and available when and where it is needed.
By doing this, the practice supports:
- protection of IT assets (including leased and rented IT assets):
- against theft, damage (virus or material degradation), and loss
- considering related contracts (software, cloud, maintenance).
- traceability of IT expenditures, ROI assessment, and optimization of the value for money
- compliance with:
- contracts, including software license agreements
- regulations (finance, taxes, electronic waste)
- the organization’s policies (security, HR, architecture, sourcing).
- a timely, informed, and appropriate response to industry trends and practices, as well as those of specific vendors (audits, cloud migration).
IT assets within organizations are used by the organization or provided to service consumers as part of the organization’s services. In the latter case, IT assets are typically accessed by service users as part of the service consumption. People using IT assets for service delivery or service consumption are called IT asset consumers.
Definition: IT asset consumer
A role responsible for an IT asset during its use for service delivery or consumption. The role can be performed by a member of the service provider organization or by a customer.
2.2 Terms and concepts
2.2.1 Organization’s assets and IT assets
Depending on the approach, different stages in the lifecycles of IT assets will be considered acquisitions. Some IT assets become a fixed asset before entering the IT asset lifecycle. What the organization acquires must be recorded in the appropriate accounts and, if deemed a capital (fixed) asset that has depreciated over several years, certain components such as accessories may be exempt based on, for example, cost.
As a result, many IT assets are also fixed or financial assets, which introduces the need for reconciliation between these two perspectives but also gives an opportunity to exchange information. For example:
- the accountant can track expenditures to identify and remove discarded IT assets from the accounts
- the IT asset manager can identify the IT components acquired by the organization that are missing from the inventory.
Therefore, the ITAM practice can benefit from involving the people in charge of the corresponding financial IT assets and their procurement.
2.2.2 Interdependence between IT assets
IT asset management should be integrated with the organization’s general asset management; however, there is also interdependence within the practice and amongst IT asset types. For example, to properly record the number of software licenses that are consumed, it is worthwhile to:
- Conduct a software inventory across all:
- relevant environments (development/integration, test, staging, live/production, training, and so on)
- platforms (on premise hardware, cloud, managed datacentres, and so on)
- Consider all deployment techniques (machine cloning, software vendor’s DVD, containers, and so on)
- Collect all parameters used in the licence model.
To be successful, software IT asset management should not be planned in isolation from the management of other types of the organization’s assets, as shown in Figure 2.1.
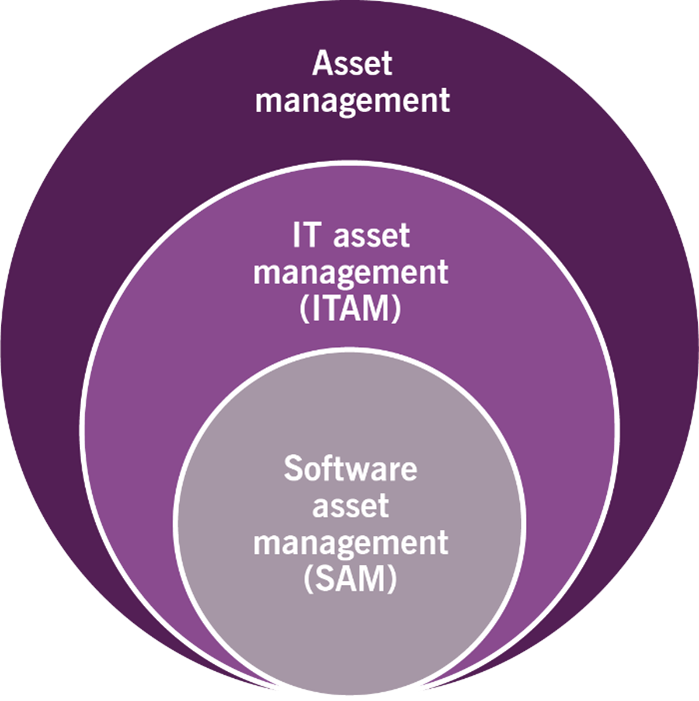
Hardware IT asset management and software IT asset management have been part of the ITAM practice from the beginning. In recent years, the demand for cloud platforms has significantly reduced the volume of licenses deployed on physical machines and increased the share of the budget spent on public cloud providers. This fundamental shift involves integrating cloud services into the ITAM practice’s scope to avoid a dramatic increase in cloud expenses and software non-compliance.
2.2.3 Progressive implementation of the IT asset management practice
It is better for organizations to start the ITAM practice as early as possible, as it will be easier to keep the IT asset information up to date. However, many organizations understand the importance of comprehensive ITAM only when they already have a large heterogeneous collection of IT assets. For these organizations, an iterative approach is recommended, in line with the ITIL 4 guiding principles.
The ISO/IEC 19770-1:2017[1] standard suggests a progressive approach in three tiers:
- obtaining trustworthy data about IT assets
- having an integrated management of their lifecycle
- optimizing efficiency and cost-effectiveness.
This means that the organization may choose to structure its ITAM practice implementation as a modular set of capabilities to be gradually activated as it is scaled up with:
- corresponding policies (applicable to all cases or to certain types of IT assets)
- procedures, work instructions, and responsibility matrices
- special recommendations attached to IT asset types (for example, the purchase of software licenses, different from the purchase of hardware).
The scope of the ITAM practice is generally too large for a one-shot implementation. Therefore, according to the ‘start where you are’ and ‘progress interactively with feedback’ guiding principles, it is advised to define it as a combination over three categories as shown below.
[1]https://www.iso.org/obp/ui/#iso:std:iso-iec:19770:-1:ed-3:v1:en [Accessed 14th April 2020]
Below is an example of a progressive scope implementation for the ITAM practice.
Example of progressive scope implementation for the ITAM practice
what (IT assets to be managed):softwarehardwarecloud servicesassociated services, such as maintenance and supportcorresponding IT asset data.where (parts of the organization concerned)countries, regions, sitesbusiness units, IT departments, service desk, procurement, finance/accounting departmentexternal service providers, such as contractors.how (process activities carried out with related policies and corresponding roles and responsibilities):to get complete and accurate datato achieve integration with other practicesto optimize IT asset-related costs and risks.The idea is to capitalize on achievements to move forward considering the organization’s priorities. For example, an organization may plan its ITAM practice scope in time with small increments. For example:initial scope:what: PC hardwarewhere: Francehow: consolidated IT asset register between IT and finance with weekly data verification.first scope expansion:what: PC hardwarewhere: Moroccohow: consolidated IT asset register between IT and finance with weekly data verificationsecond scope expansion:what: most common office software on PCswhere: first in France and then Moroccohow: consolidated IT asset register between IT, finance, and software vendors with weekly data verification.third scope expansionwhat: PC hardware and most common office softwarewhere: first in France and then in Moroccohow: management of the beginning and end of the IT asset life cycle (procurement and disposal) in collaboration with procurement and finance.
The scope increments should be chosen considering the effort of collecting, cleaning, standardizing, and migrating existing data, which can be resource-consuming.
Key message
Whether the adoption of the ITAM practice in an organization follows an iterative, progressive, or a ‘big bang’ approach, it should be based on the needs of the organization and other stakeholders. The practice aims to help maximize value, control costs, manage risks, make decisions, and comply with requirements. Scoping and implementation decisions should be verified against these objectives first to prevent excessive and unjustified efforts and costs.
2.2.4 IT asset register
The ITAM practice requires accurate inventory information, which should be kept in an asset register. The IT asset register is the main source of the IT assets’ data.
Definition: IT asset register
A collection of information about IT assets that includes their ownership, cost, and other key characteristics. The IT asset register makes it possible to maintain the stock count of IT assets.
The IT asset register is created when the ITAM approach is formed and is updated constantly during the IT assets’ lifecycles.
The IT asset register data structure may include entities, attributes, relationships, naming standards, lifecycle stages, interfaces between the IT asset register and related tools, role-based access, and so on. Data structure should consider efficient tracking, labelling, inventory, monitoring and reporting, integration and data exchange with other practices, as well as data exchange and consolidation between functional departments.
Since tracking can be very technology-dependent, ITAM practitioners should consider the constraints of an out-of-the-box data structure, the features of the existing IT asset register and ITSM tools, and the existing naming and recording conventions for the service configuration management, service financial management, and supplier management practices. Reconciliation keys and data synchronization rules between data repositories are essential to enable trustworthy information while optimizing human workload. The data structure should also define media libraries and support for the hardware stores.
If the IT asset register is created from scratch, then existing data (for example, spreadsheets) should be organized, normalized according to the new naming conventions, and uploaded to the register database.
To maintain the IT asset register, organizations periodically run inventory checks covering all IT assets, including manual or semi-automated searches for equipment on the premises and verification of the IT asset stocks in hardware stores and definitive media libraries.
To keep the IT asset register up to date, a procedure should be established to record acquired IT assets in the register. The data could be captured from the fixed IT asset register or the IT operational expenses list provided by the service financial management practice, IT asset purchase orders, suppliers’ invoices, and delivery/reception slips. The most efficient way is to embed IT assets register updates into purchasing and procurement procedures.
2.2.5 IT asset types
IT asset types typically include:
- hardware, including:
- end-user devices, such as personal computers, tablets, smartphones and SIM cards
- network and telecom equipment, such as routers, switches, load balancers, and video- conferencing and voice over Internet protocol systems
- datacentre hardware, such as servers, storage and backup systems, and uninterruptible power supplies
- significant peripherals, such as personal printers, monitors, scanners, and multifunction printing systems.
- software running on hardware and virtual machines in all environments (development /integration, test, staging, live/production, training), such as:
- operating systems
- middleware, such as web servers, SSL certificates, enterprise service buses, and database access services
- personal and server applications.
- cloud services that are increasingly replacing hardware and some software (depending on the service model), including:
- infrastructure as a service
- platform as a service
- software as a service.
- data.
Organizations experience the impacts of data leaks, cyber-attacks, and regulations about data (such as the European general data protection regulation). Therefore, to be in a better position to face these challenges, organizations may choose to manage information and data as IT assets. This can be done by:
- managing the IT assets that contain data
- applying ITAM procedures to this data to control its lifecycle.
2.2.6 IT asset lifecycle and lifecycle model
Definition: IT asset lifecycle
The various stages in the life of an IT asset from planning to disposal. The lifecycle consists of stages represented by the statuses and the status transitions that are permitted, based on the IT asset type.
The IT asset goes through the following stages in its lifecycle:
- IT asset planning and budgeting
- IT asset acquisition
- IT asset assignment (install, move, add, change IMAC)
- IT asset utilization optimization
- IT asset decommission
- IT asset disposal.
2.2.6.1 IT asset planning
The IT asset manager discusses stakeholders’ needs and, based on the market and vendor data, price, and cost model, the manager plans the best method of acquiring an asset. This is through purchase, upgrade, replacement, subscription, leasing, and so on. This enables budgeting the asset acquisition with procurement and finance.
2.2.6.2 IT asset acquisition
This activity is triggered by an approved request for procurement. The person responsible for ITAM reviews the request and checks the availability of the asset. In cases of shortage, they would check the asset model substitution rules. If the asset cannot be provided, the acquisition procedure starts.
A person or team responsible for IT asset purchasing sources the asset. The role of the ITAM practice is to ensure the optimal use of the existing assets and that all documentation regarding the purchase is captured and stored. This includes asset-related contracts (such as license, maintenance, warranty, support), invoices, proof of purchase, entitlements, license keys, maintenance activation information, and so on. The documents may be stored in the definitive media library or any other secure location, with reference to them and their location in the IT asset register and/or the content management database.
As a result of this stage, there should be a verified proof of license purchase/entitlement/service subscription, as well as a recorded IT asset with unique identification and other required information according to the agreed model in the IT asset register. Where agreed, the IT asset should have a recorded fixed asset or an expense item that is cross referenced.
2.2.6.3 IT asset assignment
Definition: IT asset assignment
The act of delegating responsibility for an IT asset to an IT asset consumer for the period of IT asset consumption/use. For some types of IT assets, they can be combined with the relevant install, move, add, change actions.
This activity includes assigning actions to the IT asset, usually IMAC.
Asset assignment is usually triggered by an approved request for asset assignment or a detected asset data gap. The person responsible checks that an available asset or eligible substitute is in stock, then follows the asset assignment procedures. It may be governed by rules for the movement of asset stocks, bring your own device (BYOD) policies, or practical guidance about the installation and use of assets to streamline costs and risks.
Asset assignments must be logged in the IT asset register. Capturing the IT asset information at this stage of lifecycle is crucial, as it decreases the need for dedicated verification efforts, like running inventories and audits. Also, this stage provides the most monitoring data, which is used to enforce policies, ensure controls, and verify the IT asset register data.
2.2.6.4 IT asset utilization optimization
Optimizing asset utilization requires understanding the contracts and pricing models.
This procedure includes:
- Adapting the stock of hardware and licenses to facilitate supplies according to service level agreements (SLAs).
- Analysing IT asset characteristics and contracts and proposing practical guidance for optimal usage. For example, adapting the installation procedure for a database engine or a virtual machine to minimize license utilization, charging for allocated assets (such as licenses, hardware, and cloud instances) by the month to encourage their decommissioning when they are not needed anymore, and so on.
- Aligning IT asset contracts with SLAs.
- Tracking and assessing the potential impacts of changes to IT assets.
- Collaborating with the service configuration management practice and others to define and track IT assets’ dependencies and be able to assess risks to the services that the change of IT asset might bring (e.g. changes to related contracts, budgets, terms and conditions, license utilization, policies or regulations, and so on).
Monitoring provides data to establish the utilization optimization, like periods of inactivity, trends in usage, license capacity issues, billing trends, and any other aspects of IT asset utilization. As part of the utilization management, ITAM practitioners should monitor and action IT asset key dates, such as end of contract or support, product/model obsolescence, expiration dates in the IT asset register (licenses, loans, SSL certificates, warranty, contract renewal, true-up, and so on). Based on this monitoring, they can create requests for procurement, asset decommissioning or asset assignment to the service request management or change enablement practices.
2.2.6.5 IT asset decommissioning
Definition: IT asset decommissioning
The act of retrieving/recovering IT assets from a consumer, particularly through uninstallation (including deletion of data according to security policy) and deciding whether the IT assets should be returned to stock or disposed of.
IT assets are decommissioned based on the request from the service request management or change enablement practices. Other causes could include end of loan or asset reservation, obsolete or useless IT asset identified in an inventory, or a stolen/lost IT asset. Before decommissioning, the asset change impact must be assessed, the decommissioning condition must be verified with potential corrective actions, and a decision should be made on reusing or disposing of the asset.
The decommissioning should follow the policies and procedures defined in the lifecycle model.
While decommissioning, data should be handled according to the information security policy and licenses should be recovered for re-use when applicable. Finally, the IT asset register should be updated.
2.2.6.6 IT asset disposal
Definition: IT asset disposal
The act of permanently removing an IT asset that is no longer in use in the organization in an appropriate and documented manner
The formal disposal procedure could be carried out in many forms, depending on asset type and acquisition method. An asset can be sold, returned, given, or destroyed following the regulations (e.g, e-waste).
During disposal, any contracts or licenses connected to the IT asset should be terminated, including maintenance contracts, and the IT asset register and relevant financial data should be updated. Definitive media library (DML) content connected solely to the asset could be archived.
2.2.6.7 IT asset lifecycle models
Each stage of the lifecycle requires different support and control activities and different types of information, depending on the type of IT asset. IT asset types may serve as a basis for creating the IT asset management approach and models.
Definition: IT asset lifecycle model
A detailed description of the organization’s approach to the management of the IT asset lifecycle tailored for a specific IT asset type.
Lifecycle models should define the processes, controls, and procedures for the IT assets handling based on the IT asset type.
Typically, each IT asset type is supported by a specialized IT asset lifecycle model. IT assets are grouped into types based on their features. This includes, but is not limited to:
- reporting cycles
- financial significance
- level of tangibility (from very tangible hardware equipment, to intangible licenses, cloud computing capacity, services or subscriptions, and so on)
- location (e.g. physically on the premises, physically in co-location or on the provider’s premises, cloud resources, licenses on own servers, and so on)
- level of immediate control (e.g. hardware boxes located on the premises or in a co-location space with restricted access, virtual servers administered by own personnel or by a third-party support team)
- longevity and rate of depreciation
- rate of change intrinsic to the IT asset and level of formality required for changes (e.g. online application subscription with continuous deployment, operating system with a three-year release cycle, or a large UPS box or some sealed device provided by government agency)
- type of IT asset acquisition (e.g. an application developed in-house, a licensed application tailored and implemented as a project, a ready-to-install a licensed application, a purchased hardware box, and so on)
- inventory and record keeping.
IT asset lifecycle models typically include:
- IT asset stakeholder group
- IT asset reporting cycle
- services dependent on the IT asset
- IT asset utilization optimization techniques and methods
- controls and procedures for the IT asset lifecycle stages
- IT asset monitoring methods and procedures
- IT asset audit and inventory methods, controls, and procedures
- IMAC procedures
- IT asset decommission and disposal methods, controls, and procedures
- shared support and maintenance procedures
- shared legal and compliance regulations, policies, and controls
- labelling and naming conventions.
For each model, a set of controls and procedures should be created to help support the lifecycle of any individual IT asset.
Activity implementation may vary depending on IT asset types. For example:
- The disposal of software is subject to the license agreement while the disposal of hardware is subject to electronic waste regulations.
- The disposal of hardware or a cloud service involves the secure deletion of data contained in it but is unlikely to involve software licenses.
Table 2.1 shows examples of the differences in handling the IT assets of different types.
Table 2.1 examples of the differences in handling the IT assets of different types.
| Lifecycle stage | Software licenses | Hardware | Hardware |
|---|---|---|---|
| Acquire IT asset | Subscribe maintenance Collect, safely store, and verify the accuracy and authenticity of the proofs of purchase Accept delivery Record license keys Add the licenses in the IT asset register | Subscribe maintenance Unpacking test Accept delivery Label Setup standard default configuration Safely store Add equipment in the IT asset register Assign installed software | Verify compliance with security policy Verify compatibility with license terms and conditions of software to be installed Add the cloud assets in the IT asset register |
| Allocate / assign IT asset | Suggest free or cheaper alternative Verify compliance with product usage recommendations, license terms and conditions, and BYOD policy Check available stock or the possibility to activate the license prior to acquisition Potentially trigger optimization, license transmission, or acquisition Activate the license Record the assignment in the IT asset register | Check available stock Potentially trigger optimization, stock transfer, or acquisition Record the assignment in the IT asset register | Record the assignment in the IT asset register |
| Optimize IT asset utilization | Identify assignees who have left or will soon leave the organization Measure frequency/level of use Investigate the usefulness of the assigned license Propose/impose decommissioning or downgrade in exchange for a discount if the price plan allows it, with the possibility to reallocate later in case of need | Identify assignees who have left or will soon leave the organization Measure the system loadIdentify and locate equipment that cannot be found on the network Investigate the usefulness of the assigned hardware Propose/impose decommissioning or downgrade, in exchange for a discount if the price plan allows it, with the possibility to reallocate later in case of need | Identify assignees who have left or will soon leave the organization (SaaS) Measure frequency/level of use (SaaS) Measure the system load (IaaS and PaaS) Investigate the usefulness of the assigned cloud assets Propose/impose decommissioning or downgrade in exchange for a discount if the price plan allows it, with the possibility to reallocate later in case of need |
| Decommission IT asset | Verify the contractual ability to reuseUpdate IT asset register | Test and recondition Decommission installed software Securely erase data Setup standard default configuration Safely store Update IT asset register | Backup data and configuration for potential later use Decommission installed software Update IT asset register |
| Dispose of IT asset | Unsubscribe maintenanceVerify the contractual or legal ability to resellUpdate IT asset registerNotify service financial management | Unsubscribe maintenance Comply with e-waste regulations Update IT asset register Notify service financial management | Unsubscribe service Update IT asset register Notify service financial management |
IT asset lifecycle types and respective models could also serve as a scope expansion unit. An organization may start the IT asset management practice with a limited scope of two IT asset types (e.g. hardware devices and software licenses) and then expand the scope by adding other IT asset lifecycle models.
2.2.7 Verification and audit
To provide stakeholders with trustworthy data about IT assets, the ITAM practice ensures IT asset data availability and accuracy.
This practice ensures that the relevant IT assets’ data is captured in the IT asset register at each stage of the lifecycle. The ITAM practice should ensure that movement and changes in IT assets are captured as early as possible. To do that, IT asset movement record-keeping should be automated where possible. Capturing the IT asset data improves the reliability of the IT register data and decreases the need for verification, but does not remove it.
Definition: Verification
An activity that ensures that a new or changed IT service, process, plan, or other deliverable is complete, accurate, reliable, and matches its design specification.
In the ITAM practice, verification is a continuous activity of identifying and correcting the gaps and deviations between the IT asset register data and the actual IT infrastructure, or data from IT assets, inventory or discovery.
Definition: Inventory
Data collection and clean-up performed to build or verify the IT asset register data.
Discovery is used to initially fill in the IT asset register if an organization has not previously kept any records, or to find some additional IT assets that were not recorded.
Definition: Inventory
The location and identification of IT assets that may exist in the organization, particularly those that may not have been recorded in the IT asset register.
The IT asset register indicates what should be found, while inventory and discovery reveal what is found. The identification and resolution of gaps between what should be found and what is found, verification (often referred to as ‘reconciliation’), is fundamental. Such reconciliation may:
- trigger an investigation concerning an unknown component found in the organization’s network
- help to identify and remove an unapproved software that the user has installed
- help to identify an IT asset that was probably stolen or lost.
Therefore, the decision to replace any content of the IT asset register with inventory or discovery data must be made with extreme caution because it can lead to a total loss of control, which is risky because the recentness of the inventory and discovery data may incorrectly suggest its relevance.
Having the valid information on the organization’s IT assets may have a critical impact on compliance.
Definition: Compliance
The act of ensuring that a standard or set of guidelines is followed, or that proper, consistent accounting or other practices are being employed.
Some examples may include compliance with software agreements, electronic waste and recycling regulations, financial regulations, and security policies.
To ensure compliance, the organization can run internal and external audits.
Definition: IT assets audit
A planned, structured, and documented inspection of an organization’s IT assets, including data collection, examination, verification, and correction activities that may be initiated and upheld by internal or external parties.
Auditing is one of the tools of the IT asset verification. Verification is a continuous background activity, and an audit is a planned verification endeavour.
Verification and auditing should become an integral part of the ITAM practice to ensure that IT asset data is valid and available for the stakeholders.
2.3 Scope
For the chosen types of IT assets, The ITAM practice maintains and provides:
- trustworthy data about what the organization has in order to be able to manage it
- means for the appropriate handling of IT assets according to policies and regulations and in consideration of applicable costs and risks
- IT asset lifecycle integration with other practices to achieve greater efficiency and cost-effectiveness.
There are several activities and areas of responsibility that are not included in the ITAM practice, although they are still closely related to ITAM; in some cases, ITAM depends on these activities. These are listed in Table 2.2, along with references to the practices in which they can be found. It is important to remember that ITIL practices are merely collections of tools to use in the context of value streams and should be combined as necessary depending on the situation.
Table 2.2 Activities related to the ITAM practice described in other practice guides
| Activity | Practice guide |
|---|---|
| Managing CI attributes and relationships in the CMDB | Service configuration management |
| Budgeting, accounting, and analysing financial data of IT assets in the context of the products and services | Service financial management |
| Sourcing and procuring of the IT assets Managing vendor contracts | Supplier management |
| Fixing IT asset technical issues | Incident management |
| Analysing the impacts of changes that involve IT assets Authorizing and planning changes requiring IT asset assignment or decommissioning | Change enablement |
| Defining spare requirements considering SLAs and potential incidents Requesting IT asset replacements when reliability is insufficient | Problem management |
| Defining minimum stock levels in the acquisition process to meet provisioning obligations in SLAs Ensuring service contracts for IT assets appropriately support SLAs | Service level management |
| Educating and training deployment teams to ensure that they know and apply practical guidance about the installation and use of IT assets Communicating to users the practical guidance about the use of assigned IT assetsEnforcing IT asset policies with contract of employment and/or IT charter for employees and contractors | Workforce and talent management |
| Monitoring and modelling the past utilization of IT assets and related services Forecasting needs for IT assets and related services considering the organization’s outlook in terms of activity, projects, programmes, and portfolios | Capacity and performance management |
| Defining optimal technical architectures considering IT asset policies, IT asset cost and risks, and practical guidance about the installation and use of IT assets | Architecture management |
| Securing the access to IT asset data in the IT asset register, and to the DMLs and hardware stores Defining procedures to handle stolen or lost IT assets | Information security management |
| Defining required IT assets and related services for service continuity plans Taking appropriate measures to protect IT assets in case of disaster, particularly those needed for service continuity plans | Service continuity management |
| Managing the request catalogue with related IT assetsDefining service pricing to encourage cost-efficient usage of IT assets and related services | Service catalogue management |
| Approving requests for ITAM or decommissioning Managing service requests to provide, move, change, or recover/reclaim IT assets | Service request management |
| Installing and uninstalling IT assets according to practical guidance about the installation and use of IT assets Using hardware stores and DMLs | Deployment management |
| Routinely checking assigned IT assets during interactions with users Explaining to users the IT asset model substitution rules and the IT asset model specific policies (for example about BYOD) | Service desk |
| Defining and managing strategic transformations (for example, mergers and acquisitions) considering IT assets and related contracts (notably the transferability of licences) | Strategy management |
2.4 Practice success factors
Definition: Practice success factor
A complex functional component of a practice that is required for the practice to fulfil its purpose.
A practice success factor (PSF) is more than a task or activity, as it includes components of all four dimensions of service management. The nature of the activities and resources of PSFs within a practice may differ, but together they ensure that the practice is effective.
The ITAM practice includes the following PSFs:
- ensuring that the organization has relevant information about its IT assets throughout their lifecycle
- ensuring that the utilization of IT assets is continually monitored and optimized.
2.4.1 Ensuring that the organization has relevant information about its IT assets throughout their lifecycle
The focus of the ITAM practice is the ‘IT assets record-keeping’; for example, ensuring that relevant IT asset information is captured, maintained, and provided to the stakeholders when needed.
Based on stakeholders’ requirements for information about different types of IT assets, IT asset lifecycle models can be identified.
Lifecycle models define what information should be captured, recorded, and reported to the stakeholders at each stage of the IT asset lifecycle. Table 2.3 shows an example of two IT asset types.
Table 2.3 Example IT asset types
| Lifecycle stage | Physical server | Software license | |
|---|---|---|---|
| IT asset planning and budgeting | Manufacturer product and service catalogue with prices and cost models Organization’s server hardware catalogue End-of-support dates Number and impact of the incidents caused by server models Teams’ feedback about server models and related services Manufacturer announcements (strategy, commercial roadmap, mergers and acquisition) Consolidated forecast of demand from the organization about server hardware and related maintenance Plan and budget for server acquisition, upgrade, and replacement, and for the subscription of related services, considering server software license plan | Publisher product and service catalogue with prices and cost models Organization’s software asset catalogue End-of-support datesHardware compatibility lists Teams’ and users’ feedback about software products and related services Publisher announcements (strategy, commercial roadmap, mergers and acquisitions) Consolidated forecast of demand from the organization about software and related maintenance Plan and budget for software license acquisition, upgrade, and replacement, and for the subscription of related services | |
| Acquire IT asset | Purchase requirements and approved requests for procurement Available servers and parts in hardware stores Server model substitution rules in case of shortage Rules governing the movement of hardware stocks Purchase orders, invoices, and delivery/reception slips Acquisition date Recorded server with unique identification and other required information Bar code, IT asset register ID, serial number, SKU code Recorded expenses cross referenced with the corresponding server Server ownerDates to be monitored (end of leasing, renewal, end of warranty)Server-related maintenance, warranty, and support contracts with service activation information | Purchase requirements and approved requests for procurementAvailable licensesLicense/product substitution rules in case of shortageRules governing licence transfersPurchase orders, invoices, and delivery/reception slipsRecorded licenses with authenticated proofs of purchase, entitlements, license activation keys, software tag, SKU codeAcquisition dateRecorded expenses cross referenced with the corresponding licensesLicense ownerDates to be monitored (license expiration, true up, maintenance renewal, end of support)Software product-related license and support contracts with service activation information | |
| Allocate/ assign IT asset | Organization’s server hardware catalogue Available servers with hardware store locations Server model specific policies (for example, Cloud options or regarding security) Server/parts model substitutions and stock movements Server-related approved changes Related server CI Approved hardware characteristics (CPU, memory, firmware, Server custodian and assignee Server location with local contacts Date and operator of IMAC Dates to be monitored (agreed upgrade, proactive maintenance, return to stock) | Organization’s software asset catalogue Available licenses License activation keys and installation media Software-related policies (for example, about BYOD) License/product substitutions and license transfers Software-related approved changes and service requests Practical guidance about optimal installation and use of software considering license models and contracts Related software CI License custodian and assignee Characteristics used to calculate license utilization (technical configuration of the platform running the software, location, user information) Date and operator of IMAC Dates to be monitored (expected installation of booked licences, end of loan) | |
| Optimize IT asset utilization | Measured or predicted system load reports Report on actual server utilization compared to forecasts Requests for change to optimize hardware value for money Servers and spare parts stock rotation reports Feedback regarding the value for money and adequacy of server-related services | Measured software usage reports Detected breach records regarding practical guidance about software installation and use Software compliance reports Impact analysis of server changes on software license utilization Requests for change/service requests to get back/substitute unused or underutilized licenses | |
| Decommission IT asset | Decommissioning date and operator Decision (return to stock, to be disposed, transferred)Proof of handling according to policies | Detected unapproved installation/usage (software piracy, blacklisted product)Decommissioning date and operator Decision (return to stock, to be disposed, transferred) | |
| Dispose IT asset | Disposal date and operator Disposal reason (obsolete, out of order, damaged, stolen) Decision (return to lessor, resale, destruction, donation)Proof of destruction according to e-waste regulations | Disposal date and operator Decision (resale, scrapping, donation) | |
For some IT asset types, an organization may decide to include IT asset lifecycle management activities, such as procurement, stock management, or transportation, in the scope of this practice. Others prefer to limit its scope to the IT assets record keeping and leave the related physical activities in the scope of other practices (including the supplier management, infrastructure and platform management, and deployment management practices, and so on).
Key message
IT asset information should be relevant to the organization’s needs. There is no benefit in including all available data in an IT asset register or in blindly following examples from publications or other organizations. ITAM practice is only as valuable as the information it provides is accurate, up-to-date, reliable, comprehensible, easy to use, and relevant. Even high-quality data is useless if it is not relevant to the organization’s needs. The careful selection of relevant data and optimal ways to maintain it is a key component of the organization’s ITAM approach.
2.4.1.1 Managing all IT assets across their lifecycle in synergy with related practices
The activities of collecting, managing, and providing IT asset information are not performed in isolation. Contrary to that, most of the related activities are performed in the context of the organization’s value streams, with many other practices involved. Working in the context of a value stream, people often do not distinguish between the practices they apply. Recommendations and procedures from the change enablement, IT asset management, and service configuration management practices can be used within one practical action, for example, relocating equipment. It is important to ensure that the relevant elements of the ITAM practice are included in the organization’s value streams and consistently applied in line with the organization’s approach to ITAM.
Following the ‘optimize and automate’ guiding principle, routine tasks (discovery, inventory, utilization, data gap analysis) should be optimized and automated to streamline workloads and IT asset utilization (underused IT assets are called sleeping stock).
In line with the ‘keep it simple and practical’ guiding principle, the practice should not be implemented as a bureaucratic control system. On the contrary, it should make everyday life easier for both consumers and the service provider’s teams by providing them with adequate and valuable IT asset information in a convenient and useful form. This provision of information typically involves channels managed as part of other practices (including the supplier management, and service desk, and service catalogue management practices, among others). The effective integration of practices is essential for IT asset information consumers to have a positive experience.
2.4.1.2 Ensuring that IT assets and related information are protected and compliant
Special effort should be made to ensure that the IT assets’ data is up-to-date, protected, and compliant with policies, laws and regulations, and agreements. Continual verification and periodic internal audits of IT assets should be performed to ensure that IT asset data meets the requirements. Internal verification and audits also help to minimize the financial, operational, psychological, and other impacts of external audits, especially when internal procedures follow the same or similar approaches.
The required evidence to demonstrate compliance of IT assets with contracts, regulations, and policies (notably security policies) should be identified.
The ITAM practice should help protect the organization from stolen, lost, or misused IT assets with, for example, secure stock facilities, quick detection of missing IT assets, practical guidance about the optimal way of handling, using, and disposing of IT assets, and so on.
2.4.2 Ensuring that the utilization of IT assets is continually monitored and optimized
The ITAM practice is not only about keeping asset records; it should help to continually optimize asset utilization. This is possible when relevant information about asset utilization trends in the organization is combined with a good understanding of the industry development trends and associated risks and opportunities. Initiatives such as migration to the cloud are often triggered and always supported by IT asset information. Monitoring of IT asset utilization can help to optimize contracts with vendors and suppliers, decrease IT asset ownership and utilization costs, and improve the financial performance of the organization and its services. The early detection of unused or under-utilized IT assets, redundant contracts, and excessive license pools helps to eliminate unnecessary spending.
IT asset utilization monitoring is based on data collected and analysed in conjunction with other practices, including the monitoring and event management, service financial management, service configuration management, service level management, and supplier management practices, among others.
ITAM specialists should regularly monitor the evolution of technology solutions (hardware, software, cloud, Internet of Things, and so on) and review the ITAM approach to mitigate risks and leverage the opportunities. Relevant information can come from vendors (product catalogues, standard contracts, strategy announcement, product obsolescence, mergers and acquisitions), or many other sources, such as press articles, white papers, market analysis, professional forums, and conferences. IT asset managers should discuss findings with peers and experts to understand the consequences and plan actions to take advantage of developments or avoid adverse consequences by negotiating, changing policies, or evolving the IT asset catalogue.
2.5 Key metrics
The effectiveness and performance of ITIL practices should be assessed within the context of the value streams to which each practice contributes. As with the performance of any tool, the practice’s performance can only be assessed within the context of their application. However, tools can differ greatly in design and quality and these differences define a tool’s potential or capability to be effective when used according to its purpose. Further guidance on metrics, key performance indicators (KPIs), and other techniques that can help with this can be found in the measurement and reporting practice guide.
Key metrics for the ITAM practice are mapped to its PSFs. They can be used as KPIs in the context of value streams to assess the contribution of the practice to the effectiveness and efficiency of those value streams. Some examples of this are given in Table 2.4.
Table 2.4 Examples of key metrics for the practice success factors
| Practice success factors | Key metrics |
|---|---|
| Ensuring that the organization has relevant information about its IT assets throughout their lifecycle | Stakeholder satisfaction with IT asset information Number and impact of audit findings and non-compliances Number and percentage of requirements for IT asset information that have not been fulfilled Percentage of actual ITAM coverage compared to the amount planned/agreed in the organization’s ITAM approach |
| Ensuring that the utilization of IT assets is continually monitored and optimized | Dynamics of the IT asset financial performance (return of investment, value on investment, total cost of ownership) Number and economic effect of utilization improvement recommendations implemented based on ITAM analytics Percentage of the controlled IT assets for which utilization is monitored and analysed |
The correct aggregation of metrics into complex indicators will make it easier to use the data for the ongoing management of value streams, and for the periodic assessment and continual improvement of the ITAM practice. There is no single best solution. Metrics will be based on the overall service strategy and priorities of an organization, as well as the goals of the value streams to which the practice contributes.
3. Value Streams and processes
Value streams contribution
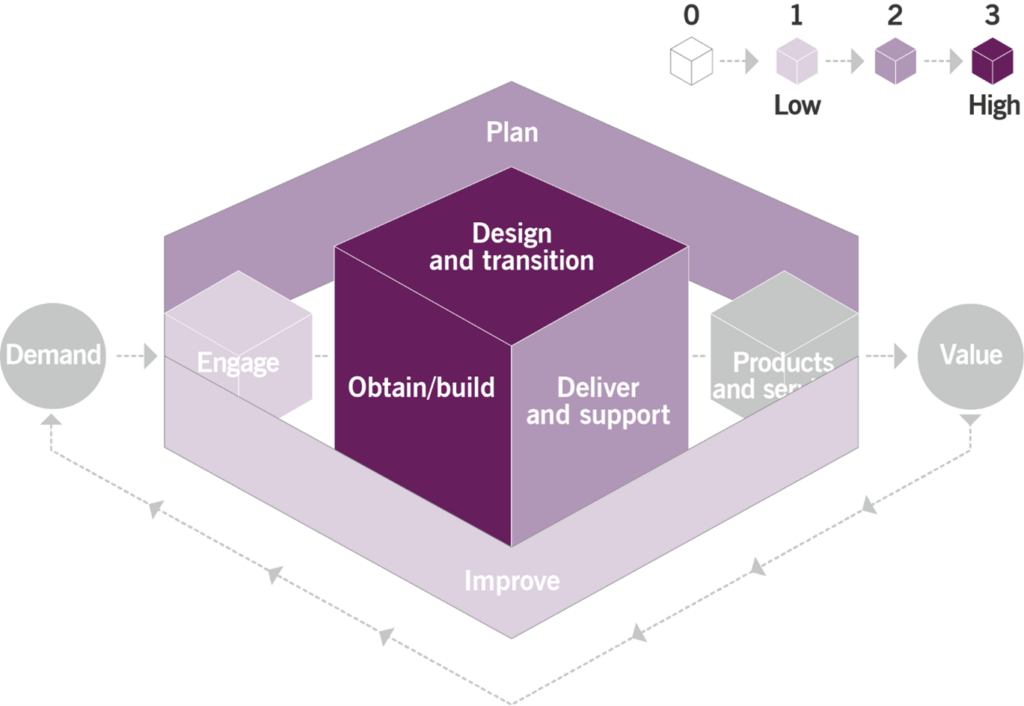
Like any other ITIL management practice, the ITAM practice contributes to multiple value streams. It is important to remember that a value stream is never formed for a single practice. The ITAM practice combines with other practices to provide high-quality services to consumers. The main value chain activities to which this practice contributes are:
- deliver and support
- design and transition
- obtain/build
- plan
The contribution of the ITAM practice to the service value chain is shown in Figure 3.1.
3.2 Processes
Each practice may include one or more processes and activities that may be necessary to fulfil the purpose of that practice.
Definition: Process
A set of interrelated or interacting activities that transform inputs into outputs. A process takes one of more defined inputs and turns them into defined outputs. Processes define the sequence of actions and their dependencies.
ITAM activities form three processes:
- managing a common approach to ITAM
- managing the IT asset lifecycle and records
- verifying, auditing, and analysing IT assets.
3.2.1 Managing a common approach to IT asset management
This process includes the activities listed in Table 3.1 and transforms the inputs into outputs.
Table 3.1 Inputs, activities, and outputs of the managing a common approach to ITAM process
| Key inputs | Activities | Key outputs |
|---|---|---|
| IT strategy and plans List of prioritized IT services Risk registers Industry and vendor trends Organization policies and external compliance requirements ITAM and IT service management tool out-of-the-box features Recognized international ITAM standards and best practices Existing IT asset data | Analyse stakeholders’ requirements and IT asset risksDefine and agree the ITAM approach Communicate and integrate the ITAM approach into the organization’s value streams Review and adjust the ITAM approach and procedures | ITAM approach IT asset register ITAM communications and knowledge management materials Requests for changes and implementation initiatives ITAM approach performance reports |
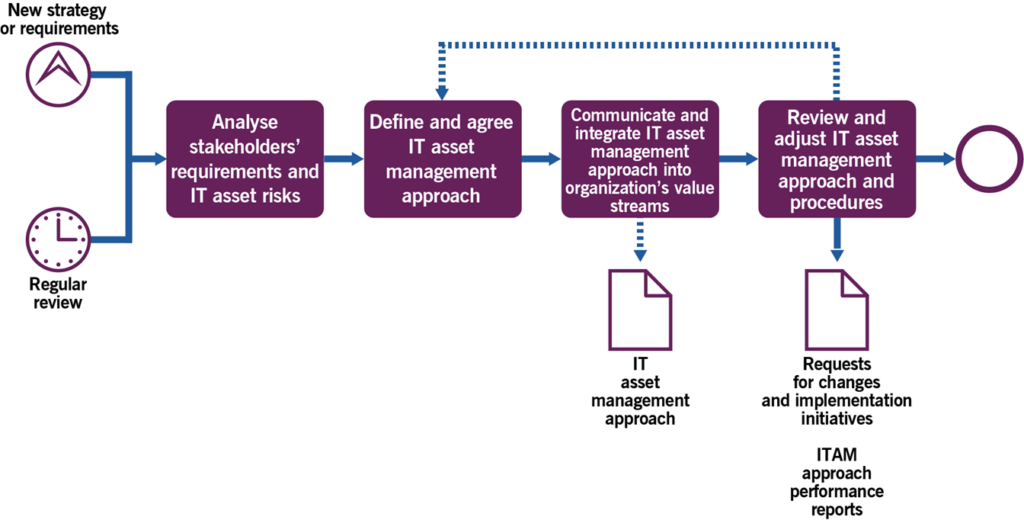
Table 3.2 provides a description of the main process activities.
Table 3.2 Activities of the managing a common approach to ITAM process
| Activity | Example | |
|---|---|---|
| Analyse stakeholders’ requirements and IT asset risks | Stakeholders in ITAM should analyse and map major hardware, software, cloud IT assets and related service expenses, IT strategy and plans (infrastructure, applications, service delivery, and so on) that are aligned with the organization’s plans, vendor trends and practices (e.g. software publishers’ compliance audits, move to the cloud), and industry trends (e.g. in hardware, software, and cloud markets). As a result of analysis and mapping, the most significant risks and opportunities (financial, legal, and technical) are identified and mapped with the associated types of IT assets. Appropriate proactive and reactive actions are defined, prioritized and drafted as part of the ITAM approach. Organizations should also conduct questionnaires/surveys, workshops, interviews with ITAM stakeholders (both internal and external to the organization) with their areas of interest (e.g. cost control, security, operational efficiency) to form a categorized and prioritized list of requirements for ITAM, aligned with the risk and opportunity register from the previous step. | |
| Define and agree the ITAM approach, scope, data structure, and lifecycle models | Based on the results from the previous activity, stakeholders should define and agree the ITAM approach. The approach defines the following: how critical ITAM is for the organization and stakeholders the type of information and level of detail on the IT assets needed by stakeholdersthe amount of resources the organization is ready to invest into ITAMthe amount of information to be captured and updatedhow detailed the policies and procedures arehow (and if) the ITAM scope will expandwhat organizational structures will support ITAMhow the IT assets tracking is organizedhow often inventory is run for different groups of IT assets.The approach can be based on any of the recognized standards for ITAM, such as ISO/IEC 19770-1.The approach typically includes: descriptions of the desired state of the ITAM practicelists of prioritized IT asset types to be included in the scopedescriptions of the required reports, supporting information, and data captured for the IT assetsIT asset data structure and lifecycle modelsIT asset policies and controlsIT asset monitoring and control proceduresIT asset verification, audit, and analysis principles and procedureslists of technology and tools used for the ITAM practice and automation.Data structures used for ITAM should accommodate the continual changes in the approach and scope. The ITAM data structure is usually the structure of the IT asset register. Data structures may include entities, attributes, relationships, naming standards, lifecycle stages, interfaces between the IT asset register and related tools, role-based access, and so on. Data structures should consider efficient tracking, labelling, inventory, monitoring and reporting, integration and data exchange with other practices, and data exchange and consolidation between functional departments.As part of the data structure definition, the IT asset register should be created (see section 2.2.4).Based on the types of IT assets defined in the approach, lifecycle models should be defined and agreed. Each lifecycle model should define controls and procedures to support the stages in the IT asset lifecycle.Different types of IT assets will require different handling of the lifecycle stages. For some IT asset types, the organization may decide to include IT asset lifecycle management activities, such as procurement, stock management, or transportation, in the scope of this practice. Others prefer to limit its scope to the IT asset record keeping and leave the related physical activities in the scope of other practices (including the supplier management, infrastructure and platform management, and deployment management practices, and so on). Also, for different types of IT assets, planning and acquisition may happen at different stages of their physical or virtual lifecycle. If budgeting and acquisition is straightforward for the hardware box, it may have more options for an application; for example, depending on the source, an in-house development or a license purchase from a vendor.Lifecycle models may have different legislation and regulations to comply with, so it may differ in policies and controls.Utilization optimization methods and procedures are also different and connected to the nature of the IT asset, as are decommissioning and disposal procedures.The IT asset manager and involved stakeholders should define and agree ITAM policies and guidelines. They should be clear, useful, easy to apply, and supported by relevant controls, including automation. Another important consideration is the alignment between ITAM policies and suppliers contracts. This is ensured in conjunction with the supplier management practice.Examples of controls and procedures for the lifecycle stages are given in section 2.2.6Stakeholders should define and agree the ITAM events to be monitored, with appropriate responses, to act as an input into the monitoring and event management practice. The main focus of IT asset monitoring should be any deviations from the established controls and policies and changes in the IT asset status. Monitoring is the most important source of data for the IT asset verification. Monitoring should be automated wherever possible. Automation tools used for monitoring could also be used for some types of audits.Monitoring should be defined to accompany IT assets in each stage of their lifecycle. Since responses to the monitoring may involve other practices or value streams, response procedures should include interfaces into other practices and value streams. Some examples include: when an unauthorized copy of a software is detected then it should be uninstalled, when a device cannot be found on the network then it must be searched for, when the maximum connections to a cloud service is almost reached then an optimization or an extra subscription should be initiated, and so on.IT asset managers should also define and agree the reports that will be produced following results of the monitoring. Reports from monitoring the IT assets serve as an input into the ITAM approach review activity, as well as the verification and audit process.ITAM stakeholders should agree how the verification, audit, and analysis works for the IT assets.Verification can be an ongoing activity of verifying and correcting the IT asset data. To achieve this, the ITAM practice should embed verification activities and controls into other practices’ procedures. For example, a support specialist can do a quick verification of a user’s desktop information using the content of the IT asset register, or an accountant can spot and report a discrepancy between IT asset data and financial data.Also, the need for a dedicated verification effort decreases if the IT asset data is properly captured and verified along the IT asset lifecycle. Therefore, like monitoring, verification should be integrated into the IT asset lifecycle, with relevant procedures for each lifecycle stage.Along with the constant verification activities, ITAM practitioners may need to run audits as a focused verification activity. The scope and frequency of the audits should be defined and agreed in the IT asset audit procedures:audit of existing IT assets at planned and random intervalsaudit of assets acquisition at planned and random intervalsaudit of IT asset-related media at planned and random intervalsanalysis and assessment of license compliancevendor compliance audits.Corrective actions based on the audit results should be addressed in the audit follow-up procedures to identify and correct IT asset data gaps.Audit results should be used for analysing IT assets. Audit results should be formatted to allow ITAM practitioners to analyse IT asset utilization and total cost of ownership and propose changes to the overall ITAM approach, as well as the IT asset lifecycle models. | |
| Communicate and integrate the ITAM approach into the organization’s value streams | The defined, agreed, or updated approach, scope, lifecycle models, and procedures are communicated and discussed with the ITAM stakeholders across the organization. Stakeholders may decide the level of formality for the training on the ITAM controls and procedures. For the people involved in the supplier management daily, policies and controls may be created for a formal training as a prerequisite and periodic awareness trainings.Some ITAM concepts deserve an effort of popularization and practical guidance to let the organization benefit from them, this includes software licenses, cloud service agreements, manufacturer’s warranties, maintenance and support, and so on.Implementation of the ITAM approach is carried out in conjunction with the configuration management, supplier management, change enablement, project management, organizational change management, workforce and talent management, and relationship management practices, among others. Communication plays an important part in integrating and embedding the ITAM approach and procedures into the wider organization. IT asset managers may choose to communicate across the organization about the ITAM approach, scope plans, implementation status, improvements based on ITAM analysis, compliance audit results, and so on. For maximum benefit, they should identify appropriate timing, content, and methods for target audiences and enable easy feedback loops.External communications on the ITAM procedures and controls, IT asset data requirements, and IT asset compliance controls should be prepared and published in the suppliers and partners information channels. | |
| Review and adjust the ITAM approach and procedures | ITAM stakeholders monitor and review the adoption, compliance, and effectiveness of the agreed ITAM approach and procedures; this is done on an event-based (IT asset-related incidents, IT asset monitoring events, compliance issues, and so on) and interval-based basis. The main input for these reviews should come from participants in the managing IT asset records process. Adapting the approach to specific requirements can improve it or jeopardize its viability. Therefore, review participants should: check the compatibility of specific requirements with ITAM policies and internal and external regulationsevaluate the impact of the specific requirements in the four dimensions of service management (IT asset management data model and tool setup; contracts with suppliers/partners/customers; processes/procedures/work instructions; organization, team structure, people’s habits and corporate culture, and so on)categorize the technical tools and automation implementations to be performed to meet the specific requirements (supporting out of the box, simple configuration, complex configuration, or specific development) evaluate the potential solutions in terms of cost, benefit, and risk.Results, findings, and initiatives are used as input for continual improvement for the ITAM practice. | |
3.2.2 Managing the IT asset lifecycle and records
This process includes the activities listed in Table 3.3 and transforms the inputs into outputs.
Table 3.3 Inputs, activities, and outputs of the managing the IT asset lifecycle and records process
| Key inputs | Activities | Key outputs |
|---|---|---|
| IT asset management approach, scope, controls, procedures, and lifecycle modelsIT asset register Risk registers Industry and vendor trendsIT asset monitoring reportsITAM and IT service management tool | Updated IT asset register IT asset utilization optimization initiatives Exception reports IT asset lifecycle reports | Updated IT asset register IT asset utilization optimization initiatives Exception reports IT asset lifecycle reports |
Figure 3.3 shows a workflow diagram of the process
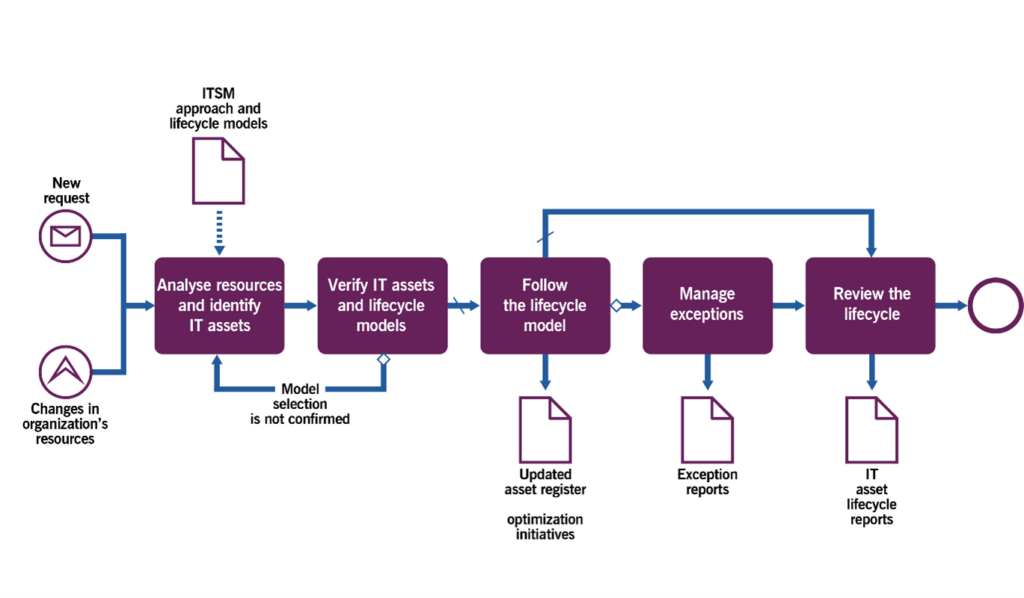
Table 3.4 provides a description of the main process activities.
Table 3.4 Activities of the managing the IT asset lifecycle and records process
| Activity | Description and recommendations |
|---|---|
| Analyse resources and identify IT assets | Upon request for a new IT asset, discovery of a new IT asset, or a change in the existing IT asset, the person responsible for the IT asset identifies the type of asset and checks if the type is in the scope of the ITAM practice. If it is, a respective IT asset lifecycle model is identified to follow. |
| Verify IT assets and lifecycle models | The IT asset manager reviews the selected IT asset type and lifecycle model and confirms that it is suitable for the asset. |
| Follow the lifecycle model | The IT asset manager and/or any member of the team responsible for the IT asset follows the selected model. This typically includes, with small variations depending on the starting point of the lifecycle in the case, the following:capturing and updating the IT asset data in the IT asset register at each stage of the lifecyclemonitoring an IT asset, enforcing controls, and analysing the IT asset monitoring data among relevant IT assetsensuring ongoing IT asset register data verification and including the IT asset in the relevant IT asset auditsensuring compliance at each stage of the IT asset lifecycleproviding up-to-date IT asset information and reports to all stakeholders, for value maximization, cost reduction, risk management, and decision making. |
| Manage exceptions | If an exception occurs during the IT asset lifecycle, the IT asset manager and the team responsible handle it in line with the organization’s ITAM approach, compliance regulations, values, and established practices. Deviation from the procedures should be taken with care, ensuring compliance and maintaining controls.Exceptions should be documented and reviewed for possible approach, scope, and lifecycle model changes, future references, and lessons learnt. |
| Review the lifecycle | Upon significant exceptions, or regularly, the IT asset manager and the team responsible should review the IT asset lifecycle models to confirm or update them based on the collected feedback, reviewed requirements, IT asset records, audit reports, and new risks and opportunities. |
Verifying, auditing, and analysing IT assets
This process includes the activities shown in Table 3.5 and transforms the inputs into outputs.
Table 3.5 Inputs, activities, and outputs of the verifying, auditing, and analysing IT assets process
| Key inputs | Activities | Key outputs |
|---|---|---|
| ITAM approachIT asset register Reports from monitoring IT assetsIT asset risk registers Internal and external compliance regulations | Plan auditCollect IT asset data Verify IT asset data Review and analyse verification and audit outputs Compose and communicate verification and audit reports | Updated IT asset registerIT asset audit reportsIT asset approach feedback Updated IT asset risk register Request for change |
Figure 3.4 shows a workflow diagram of the process.
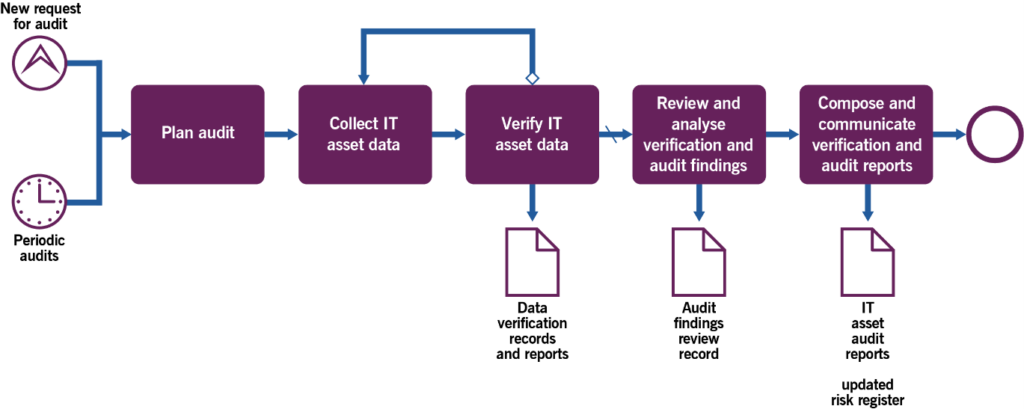
Table 3.6 provides examples of the process activities.
Table 3.6 Activities of the verifying, auditing, and analysing IT assets process
| Activity | Example |
|---|---|
| Plan audit | Audits can be planned in response to some detection of unauthorized or unregistered IT assets, before or after significant technical or organizational changes, before any important milestone with a manufacturer or a software vendor, or at a planned interval. The frequency or scope of audits should be adjusted after considering the financial stakes, risks, and detected errors. Audits should be planned where and when the most significant discrepancies could be discovered and before they penalize the organization. Automation can help increase audit frequency and scope.Plans should exist to: run internal auditspredict the likelihood of external audits (for example software compliance) and manage them when they occur.Audit plans usually include the following:a timeframe and schedulethe IT assets and organizational units in scope of the audit, for example, considering the results of previous audits or to prepare for a probable external auditthe discovery and inventory tools and techniques usedthe methods of reconciliation and verification usedthe controls and compliance regulations to be checkedthe reporting and communication planthe post-audit actions to deal with detected issues, avoid their recurrence, and improve future audits. |
| Collect IT asset data | Most IT asset data is collected by discovering, inventorying, and monitoring automated tools to enable comparison with the IT asset register. In special situations, discovery and inventory are run manually where automated discovery is not possible or financially viable.The audit should verify that the assets listed in the IT asset register exist. Any discovered IT assets should be checked for the IT asset register records. This requires that collected data covers:the acquired assets and subscribed contracts identified such as procurement, finance, supplier management, resellers, software publishers, manufacturers, and so onexisting assets in all environments (not only production ones).Audit should verify that the description and technical characteristics of the assets are correct so the format of the data collection will be as close as possible to the data model of the IT asset register to enable industrial reconciliation. Therefore, data collection generally includes clean-up and normalization.Data collection should also cover important media associated with IT assets:contractual documents (contract, proof of purchase or subscription, delivery slip, invoice, certificate of destruction in compliance with electronic waste regulations, and so on)installation media (DVD, installation package, license activation key, and so on)practical documentation (installation procedure, administration guide, maintenance activation contacts and instructions, vendor extranet, and so on).Similarly to other IT asset data, the media data collection should be automated as much as possible (digital contracts and other media), but it often requires manual work (physical media such as printed documents, DVDs, and so on). |
| Verify IT asset data | The last verification and audit date should be saved with the asset records to facilitate the scheduling of future audits. Any discrepancies found in the audit must be investigated and corrected, such as:IT asset records that do not match the corresponding IT asset present in the infrastructurediscovered IT assets that do not exist in the IT asset registerunauthorized IT assetsmissing or existing but unregistered IT asset-related mediaincorrect IT asset-related media (such as a license entitlement granted to the wrong organization, false proof of purchase, and so on).The correction of discrepancies may imply many types of actions, such as the removal of the unauthorized IT assets, the regularization of unregistered acts (acquisition, assignment, decommissioning, disposal, and so on), claims against suppliers, archiving of obsolete data, creation of a security incident record if a device appears as stolen or lost, and so on. |
| Review and analyse verification and audit findings | Results of the audit and verification should be reviewed to drive improvements and to prepare future audits. Audit data should be used for the analysis of risks, compliance assessment, costs optimization, general trends in the IT assets utilization, and ITAM approach adoption. The risk register should be reviewed for the IT assets in the scope of the audit. This activity may initiate many improvement techniques, some of which may require post-audit follow-up. For example:automation of repetitive tasks to avoid human error or reduce the workload of ITAM practitionerssimplification of ITAM solutions to increase their adoptionbetter operational integration of ITAM activities in value streams to reduce process misalignment and enable seamless customer experienceoptimization of the IT asset register structure to secure the provision of the most important datarestocking the hardware stores and media librarieseducation, penalties, and management awarenessrecommendations for the next audits. |
| Compose and communicate verification and audit reports | Based on the results of the review and analysis of verification and audit outputs, the audit report should be: formalized with concerned stakeholders to ensure they all understand and agreedistributed through the agreed communication channelssafely stored to enable future reuse for feedback or as a baseline.The owner of post-audit actions should be appointed with enough time, means and authority in order to enable achievement of approved actions, and escalation in case of difficulty. |
4. Organizations and people
4.1 Roles, competencies, and responsibilities
The practice guides do not describe the practice management roles such as practice owner, practice lead, or practice coach. They focus instead on the specialist roles that are specific to each practice. The structure and naming of each role may differ from organization to organization, so any roles defined in ITIL should not be treated as mandatory, or even recommended. Remember, roles are not job titles. One person can take on multiple roles and one role can be assigned to multiple people.
Roles are described in the context of processes and activities. Each role is characterized with a competency profile based on the model shown in Table 4.1.
Table 4.1 Competency codes and profiles
| Competency code | Competency profile (activities and skills) |
|---|---|
| L | LCompetency code |
| А | Administrator Assigning and prioritizing tasks, record-keeping, ongoing reporting, and initiating basic improvements. |
| C | Coordinator/Communicator. Coordinating multiple parties, maintaining communication between stakeholders, and running awareness campaigns. |
| М | Methods and techniques expert. Designing and implementing work techniques, documenting procedures, consulting on processes, work analysis, and continual improvement. |
| Т | Technical expert. Providing technical (IT) expertise and conducting expertise-based assignments |
The role accountable for all ITAM activities is usually the ITAM practice owner. The competency profile for this role in the context of ITAM is CLA, though the importance of each of these competencies varies from activity to activity. Examples of other roles which are responsible for ITAM activities are listed in Table 4.2, together with the associated competency profiles and specific skills.
Table 4.2 Examples of roles with responsibility for ITAM activities
| Activity | Responsible roles | Competency profile | Specific skills |
|---|---|---|---|
| Managing a common approach to the ITAM process | |||
| Analyse stakeholders’ requirements and IT asset risks | IT asset manager License manager Procurement manager Contracts manager Portfolio manager Service delivery manager Product owner Business analyst Auditor External consultants | TCM | Good understanding of the organization’s strategy, stakeholders, key services and key assets, vendor ecosystem Understanding of IT asset risks Expertise in IT asset compliance, licensing, procurement, and contracts management |
| Define and agree the ITAM approach | IT asset manager IT asset owner IT asset custodian License manager Procurement manager Contracts manager Service delivery manager Product owner Business analyst Auditor External consultant | MTC | Expertise in IT asset compliance, licensing, and technical aspects of ITAM Understanding of procurement and contracts management Expertise in ITAM, SAM tools Process and workflow expertiseRisk management |
| Communicate and integrate the ITAM approach into the organization’s value streams | IT asset manager License manager ITAM/SAM implementation project manager Service delivery manager Change manager Knowledge manager Organizational change manager Product owner External consultant | CLM | Good understanding of the organizational culture and internal stakeholders. Good knowledge of the agreed approach. Excellent leadership and communication skills |
| Review and adjust the ITAM approach and procedures | IT asset manager IT asset owner IT asset custodian License manager Procurement manager Contract manager Service delivery manager Product owner Business analyst Auditor External consultant | TMCA | Decision making Good understanding of the organization’s strategy, stakeholders, key services and key assets, and vendor ecosystem Understanding of IT asset risks Expertise in IT asset compliance, licensing, and technical aspects of ITAM Understanding of procurement and contracts management |
| Managing the IT asset lifecycle and records process | |||
| Analyse resources and identify IT assets | IT asset manager IT asset owner IT asset custodianLicense manager Procurement specialist Contract manager Service delivery manager Product owner Service desk agent Stockroom manager IT coordinator | TCA | Good knowledge of the organization’s ITAM approach, IT asset types, and lifecycle models |
| Verify IT assets and lifecycle models | IT asset manager IT asset owner IT asset custodian License manager Procurement manager Contract manager Service delivery manager Product owner IT manager | TA | Good knowledge of the organization’s ITAM approach, IT asset types, and lifecycle models |
| Follow the lifecycle model | IT asset manager IT asset owner IT asset custodian License manager Procurement /purchasing specialist Contract manager Service delivery manager Product owner Service desk agent Stockroom manager IT coordinator Accountant /financial analyst Systems administrator Developer | TAC | Good knowledge of the organization’s ITAM approach, IT asset types, and lifecycle models Good knowledge of the IT asset register and related procedures. |
| Manage exceptions | IT asset manager IT asset owner IT asset custodian License manager Service delivery manager Product owner Service desk agent Stockroom manager IT coordinator | TCAM | Good knowledge of the organization’s ITAM approach, IT asset types, and lifecycle models Good knowledge of the IT asset register and related procedures. |
| Review the lifecycle | IT asset manager IT asset owner IT asset custodian License manager Procurement manager Contract manager Service delivery manager Product owner IT manager Service desk agent Stockroom manager Accountant/financial analyst Systems administrator Developer | TA | Good knowledge of the organization’s ITAM approach, IT asset types, and lifecycle models Understanding of IT asset risks Expertise in IT asset compliance, licensing, and technical aspects of ITAM Understanding of procurement and contracts management |
| Verifying, auditing, and analysing IT assets | |||
| Plan audit | IT asset manager License manager Compliance officer Service desk lead Stockroom manager IT coordinator Accountant/financial analyst Auditor Vendor representative Government representative | TCMA | Expertise in auditing Understanding of IT asset risks Expertise in IT asset compliance, licensing, and the technical aspects of ITAM Expertise in inventory and discovery tools, stocks management, and stock taking |
| Collect IT asset data | IT asset manager IT asset custodian License manager Compliance officer Service desk agent Stockroom manager IT coordinator Accountant/financial analyst Auditor Vendor representative Government representative Systems administrator Developer | TA | Expertise in IT asset compliance, licensing, and the technical aspects of ITAM (e.g. cloud, virtualization, data management) Expertise in inventory and discovery tools, stocks management, and stock taking Knowledge of the IT asset register and ITSM tools |
| Verify IT asset data | IT asset manager IT asset custodian License manager Compliance officer Service desk agent Stockroom manager IT coordinator Accountant/financial analyst Auditor Vendor representative Government representative Systems administrator Developer | TA | Expertise in IT asset compliance, licensing, and the technical aspects of ITAM (e.g. cloud, virtualization, data management) Expertise in inventory and discovery tools, stocks management, and stock taking Knowledge of the IT asset register and ITSM tools |
| Review and analyse verification and audit findings | IT asset manager License manager Compliance officer Service desk lead Stockroom manager IT coordinator Accountant/financial analyst AuditorVendor representative Government representative Systems administrator Developer | TAC | Expertise in IT asset compliance, licensing, and the technical aspects of ITAM (e.g. cloud, virtualization, data management) Expertise in inventory and discovery tools, stocks management, and stock taking Knowledge of the IT asset register and ITSM tools |
| Compose and communicate verification and audit reports | IT asset manager License manager Compliance officer Service desk lead Stockroom manager IT coordinator Accountant /financial analyst Auditor Vendor representative Government representative | TCAM | Communication and presentation skills, data processing skills |
4.1.1 IT asset manager
The IT asset manager is responsible for overseeing the IT asset lifecycle with related data in their organization, for all IT assets in scope. This role may be local or global. In many organizations, the IT asset manager role is performed by a dedicated person, sometimes under a specialized job title: software IT asset manager, hardware IT asset manager, cloud IT asset manager, and so on.
This role is typically responsible for:
- managing the ITAM approach
- communicating ITAM approach and procedures
- integrating the ITAM approach into value streams
- making decisions about IT asset inclusion in the scope and managing exceptions
- ensuring the IT asset lifecycle models are followed
- ensuring the IT asset register contains valid data
- ensuring the organization’s IT assets are compliant
- participating in IT asset risk management
- liaising with the monitoring and event management practice and ensuring core IT asset events and changes are monitored
- optimizing IT asset utilization and reporting related financial results
- reporting on ITAM and compliance.
4.1.2 License manager
The license manager is the subject matter expert for all licensing aspects related to software and cloud products, including stock of available licenses. This role collaborates with the supplier and contract manager role to ensure IT-asset related contracts (e.g. maintenance and support) are appropriate in terms of cost/value balance, compliance, and so on. Due to the complexity and variety of licence models, the role may be (and generally is, in large organizations) dedicated to a specific platform type (workplace, datacentre) and/or to a specific software publisher. In the latter case, this role is commonly combined with the software IT asset manager role.
4.1.3 IT asset owner
The owner is the organization that keeps the rights to the IT asset and sponsors the asset.
4.1.4 IT asset custodian
This can either be a team or person that ensures the right utilization of the IT asset. They ensure that ITAM procedures are consistently applied to the IT asset throughout its lifecycle in the best interests of the IT asset owner.
4.1.5 IT asset consumer
A role responsible for an IT asset during its use for service delivery or consumption. The role can be performed by a member of the service provider organization or by a customer.
4.2 Organizational structures and teams
4.2.1 Level of centralization
Populating ITAM roles in a central team can help develop expertise and facilitate collaboration with other central functions, such as procurement, finance, and risk management. Such centralization can, however, create a distance that is detrimental to day-to-day collaboration with those who use and handle IT assets. This paradox can be managed by achieving centralization through other dimensions of service management, if the structure and culture of the organization allows it. This could include: a centralized IT asset register managed by geographically dispersed teams, a multilingual workflow engine running common processes across several time zones, the collegial governance of processes and data models to drive convergence despite the heterogeneity of implemented solutions, and so on.
Global organizations often centrally define their ITAM practice and deploy it in a decentralized manner. In such case, global convergence should be achieved considering key local aspects: the visions and goals of sponsors, process maturity, cultural shift, IT asset types and volumes, business and economic reality, gaps with convergence points covering the four dimensions of services (policies, data model, staffing), language, laws and regulations, currency and accounting systems, suppliers’ and partners’ contracts, and so on.
4.2.2 Stakeholder involvement
Conversing with IT asset consumers is essential; for example, to identify the most appropriate hardware asset model or loan terms considering stakeholders’ preferences and constraints. Depending on consumer profiles and the level of centralization of ITAM in the organization, this interaction can rely on many channels: periodic online or service request closure surveys, random phone interviews, suggestion boxes at the service desk or on the portal, periodic meetings organized by the service level management practice, customer events, a selection of hardware models with a panel of users, and so on.
4.2.3 Cultural aspects
The effectiveness of the ITAM practice depends on the organization’s culture, which can vary significantly from place to place depending on people’s perceptions of ownership and personal responsibility. The ITIL 4 practice guides for the workforce and talent management and organizational change management practices can help enable positive and sustainable change in this area.
4.2.3.1 Consciousness of financial, security, and legal stakes
People requesting and handling IT assets should understand the associated financial, security, and legal stakes for the organization. This implies constant monitoring and discussions with relevant individuals to avoid noncompliance and undesired behaviour. For example, when a free (for non-commercial usage) software is installed on a device by a user, when a machine is not returned to stock after the user has left, when a testing environment is not decommissioned from the cloud environment once the project is over, and so on.
4.2.3.2 Engagement of individual responsibility without complacency
For each IT asset custodian or consumer to take their responsibility of the IT assets seriously, that responsibility should be assigned by name. Therefore, IT assets should not be assigned to organizational units but to individuals. The potential individual consequences of transgressions (negligent loss or damage, sloppiness, improper usage, software piracy) should be clearly stated in contracts of employment, pricing plans, and disciplinary procedures.
4.2.4 Internal profit centre providing IT assets and related services
Technical teams handle the IT assets. The ITAM practice combines skills scattered in a fragmented way throughout the organization about technology, contracts, procurement, finance, laws, data, processes, taxes, suppliers, products, services, and so on. IT assets represent a significant portion of the organization’s expenses and develop stakes that are set to grow with the digital transformation.
Organizations that have a mature ITAM practice have understood this. Consequently, they do not structure their practice around a bureaucratic entity, but as an internal provider which finances itself through the margins it generates. Internal ‘ITAM as a service’ may enable value with:
- trustworthy data requiring minimal effort thanks to integrated processes and practical technology
- one-stop shopping and disposal
- transverse stock management to optimize acquisitions
- centralized management of major solution vendors in synergy with internal stakeholders to defend their interests more forcefully
- negotiated terms and conditions
- attractive prices for IT assets and related services and valuation of disposed assets
- governance of the IT asset catalogue
- consultancy, training, and awareness about tricky aspects, such as licensing, contracts, or cost optimization
- handling of external audits in project mode
- simplified collaboration between IT and non-IT organizational units (finance, procurement, legal)
- advocacy and sharing of best practices in professional associations and user clubs.
5. Information and technology
5.1 Information exchange, inputs/outputs
The effectiveness of the ITAM practice is based on the quality of the information used. This information includes, but is not limited to, information about:
- the organization’s strategy
- the organization’s architectures
- the organization’s portfolios
- stakeholders’ requirements and needs for IT asset information
- applicable regulatory requirements
- IT asset data from vendors, suppliers, and publishers
- technology trends
- IT asset utilization data
- change schedules and plans
- programme and project plans
- financial data
- service financial management policies and procedures
- service configuration data.
This information may take various forms, depending on the IT asset types, organization’s requirements, and IT asset management tooling. The key inputs and outputs of the practice are listed in section 3.
5.2 Automation and tooling
Ensuring that IT asset data is updated at every change of status of the IT asset, automating the IT asset register and, in general, capturing IT asset data is very important for the practice. Automation helps when managing the growing number of IT assets with fewer ITAM practitioners. Where automation is possible and effective, it may involve the solutions outlined in Table 5.1.
Table 5.1 Automation solutions for ITAM activities
| Process activity | Means of automation | Key functionality | Impact on the effectiveness of the practice |
|---|---|---|---|
| Managing a common approach to ITAM | |||
| Analyse stakeholders’ requirements and IT asset risks | Analytical tools Collaboration and communication tools | Risk and opportunities analysis Value impact mapping Collaboration and communication | Medium |
| Define and agree the ITAM approach | Mind mapping, brainstorming tools Workflow modelling and visualization tools, communication and collaboration tools | Workflow modelling, visualization, and mapping activities and responsibilities | Medium/high |
| Communicate and integrate the ITAM approach into the organization’s value streams | Communication and collaboration tools, presentation tools, portals | Support of promotion, training, and awareness | Medium |
| Review and adjust the ITAM approach and procedures | Collaboration and communication tools, reporting tools, and visualization tools | Collaboration, information exchange, report creation, and distribution | Medium |
| Managing the IT asset lifecycle and records | |||
| Analyse resources and identify IT assets | Collaboration and communication systemsITAM systems Workflow automation systems | Collaboration, information exchange, workflow and approval automation Data export from external data sources | Medium |
| Verify IT assets and lifecycle models | Collaboration and communication systemsITAM systems Workflow automation systems | Collaboration, information exchange, workflow, and approval automation Data export from external data sources | High |
| Follow the lifecycle model | ITAM systems Inventory and discovery tools Data tools Procurement systems Supplier and contract management databasesAccounting and financial ITAM systems Workflow management tools Labelling, barcode, and QR code reader systems Geolocation and geofencing systems | IT asset register Software IT asset management and software license optimization Mobile device management Assets inventory and discovery IT asset data reconciliation with secondary and third-party data sources Valuation and invoicing (interfaced with the IT asset register to create invoices) Workflow automationLabelling, barcodingGeolocation and geofencing | High |
| Manage exceptions | ITAM systems Inventory and discovery tools Data tools Procurement systems Supplier and contract management databasesAccounting and financial ITAM systems Workflow management tools Labelling, barcode, and QR code reader systems Geolocation and geofencing systems | IT asset register Software ITAM and software license optimization Mobile device management Assets inventory and discovery IT asset data reconciliation with secondary and third-party data sources Valuation and invoicing (interfaced with the IT asset register to create invoices) Workflow automation Labelling, barcoding Geolocation and geofencing | Medium to high |
| Review the lifecycle | Collaboration and communication tools, reporting tools, visualization tools Change and project management tools | Collaboration, information exchange, report creation, and distribution Changes and projects tracking, audit trail | Medium |
| Verifying, auditing, and analysing IT assets | |||
| Plan audit | ITAM systems Audit tools Collaboration and communication tools | IT asset register Audit actions planning and tracking Collaboration and communications | Medium |
| Collect IT asset data | ITAM systems Inventory and discovery tools Data processing tools | IT asset register Mobile device management Assets inventory and discovery IT asset data reconciliation with secondary and third-party data sources Labelling, bar-coding Geolocation and geofencing; | High |
| Verify IT asset data | ITAM systems Inventory and discovery tools Data processing tools Labelling, barcode, and QR code reader systems Geolocation and geofencing systems | IT asset register Software ITAM and software license optimization Mobile device management Assets inventory and discovery IT asset data reconciliation with secondary and third-party data sources Labelling, bar-codingGeolocation and geofencing | High |
| Review and analyse verification and audit findings | Collaboration tools Analysis, reporting and dashboard tools, and task assignment and actions tracking tools | Analysis of processing and reporting, dashboards, information visualization, decision-making support, and decision and action assignment and tracking | Medium |
| Compose and communicate verification and audit reports | Reporting and dashboarding tools | Reports creation and distribution, dashboards, data visualization | Medium |
6. Partners and suppliers
Very few services are delivered using only an organization’s own resources. Most, if not all, depend on other services, often provided by third parties outside the organization (see section 2.4 of ITIL Foundation: ITIL 4 Edition for a model of a service relationship). This means that organizations constantly handle IT assets that are provided to them as part of third-party services. Similarly, organizations’ IT assets are widely used by their service consumers. This requires effective coordination of ITAM practices between members of the service relationships ecosystem. The exact level of coordination depends on the type of service relationship. The closer the relationship and higher the trust, the more IT asset information can be shared, and management activities performed together.
Where service relationships are basic or cooperative and suppliers and partners are independent organizations with their own objectives, the organization should take steps to protect its IT assets and remain in control. These steps include the following:
- Sign non-disclosure agreements and carefully control the exchange of sensitive IT asset data with suppliers and partners.
- Discover conflicts of interest that may cause harm to the organization (such as an outsourced service desk that charges for its services based on the number of assets it provides to users, or a software compliance consulting mission entrusted to a supplier who is also a reseller or auditor on behalf of a software publisher).
- Including terms in third-party service contracts about the handling of IT assets, with clear duties and responsibilities for each ITAM activity the suppliers contribute to, such as an outsourced service desk handling activities like the reception of ordered IT assets, secure storage, stock management, allocation / IMAC, detection and handling of special situations (damage, non-compliance, loss), inventory, and so on.
- Communicating the achievements of a mature ITAM practice can help to optimize relationships with vendors and suppliers. For example, the understanding of license models and a good software compliance can discourage time-consuming vendor audits; controlling IT spending can refocus collaboration with suppliers on higher value-added topics or increase investor and customer confidence; operational activities that are free of administrative hassles can help attract talent and reduce service provider rates; and so on.
Outsourced ITAM services exist and can be helpful. However, the ultimate responsibility for an organization’s IT assets cannot be outsourced. Therefore, the organization should develop internal competencies and controls to protect its own interests and master its contractual and legal responsibilities.
7. Important reminder
Most of the content of the practice guides should be taken as a suggestion of areas that an organization might consider when establishing and nurturing their own practices. The practice guides are catalogues of things that organizations might think about, not a list of answers. When using the content of the practice guides, organizations should always follow the ITIL guiding principles:
- focus on value
- start where you are
- progress iteratively with feedback
- collaborate and promote visibility
- think and work holistically
- keep it simple and practical
- optimize and automate.
More information on the guiding principles and their application can be found in section 4.3 of ITIL Foundation: ITIL 4 Edition.